Perimeter Intrusion Detection System Considerations
Detection of a potential or confirmed breach of the property perimeter provides time for police or guard forces to intercept a threat before the loss of property or harm to staff. Facilities with perimeter detection in place range from remote petrochemical or cellular sites to vehicle processing or storage facilities to critical infrastructure.
There are many things to consider when evaluating your current or new perimeter detection strategy.
- Early warning detection and assessment
- Continuous line of detection
- Delaying intruder access
- Response force reaction time
- Threat analysis
- Risk assessment
- Single layer protection
- Dual layer protection
- Multi-layer protection


KEY PRINCIPLES OF AN EFFECTIVE PERIMETER SECURITY PROGRAM
Deter: A fortified site is the optimal deterrent to attackers. Commonly, perimeter fences / barriers, plus other visible mechanisms such as perimeter intrusion detection systems (PIDS), lighting and cameras serve as deterrents to a would-be attacker.
Detect: Implementation of detection sensors enhance the ability to identify intruders and stave off an attack. It is recommended to introduce at minimum a single layer of PIDS technology to detect intruders at the outer perimeter. Often, a dual-layer approach is called for to protect a facility with higher security requirements (i.e. potential theft or damage to higher value assets). Layering complementary technologies, such as fence sensors plus video analytics, allows reinforcement of the perimeter layer. For the highest security applications (i.e. where threat to critical infrastructure or human life is present), a multi-layered system incorporating a range of technologies further adds to the level of protection.
Delay: It’s critical to maximize the time span from ingress to attackable asset, to allow the security team time to respond. Physical barriers at the perimeter, PIDS on and inside the perimeter fence, internal barriers (ideally with PIDS), and the distance between barriers and attackable asset are all delay mechanisms that slow an attacker.
Assess: Introduce an integrated system that includes alarm communication and CCTV/Video assessment of intrusions. Operators need to see what the system has detected.
Respond: Design scenarios and deployment of your response force to stop a threat / attack or intruder.
Intelligent System Characteristics
Key components of an intelligent perimeter detection system:
- Detection
- Location
- Adaptability
- Zones & Cameras
- Discrimination
- Power & Data
- Maintenance
- Integration


Design Considerations
- Access Considerations
- Authorized Access
- Unauthorized Access
- Site Security Level Considerations
- Detection Criteria
- Deployment Examples


Rigid and Decorative Fence Considerations
When deciding that it's time to add fence protection to a rigid or decorative fence, end users often think they have limited options. In the video below, Steve Pennington and Jeff Drews discuss strategies and solutions for these types of applications. Then, Brad Castillo and Tim Claus help Jeff test a rigid fence intrusion detection solution.
During the video, we get some excellent advice about fence intrusion detection system testing:
- The cut simulator tool mimics an intruder using bolt-cutters, and an actual climber is the only accurate method to conduct a climb test.
- Testing the fence must be done from the outside (unsecured side) of the fence or it’s not a real test. Many times, customers with rigid fences will complain that they are getting nuisance alarms and are also having difficulty detecting a climber. In nearly every case, we’ve found that they are testing from the inside (secure side) of the fence.


Security Camera Field of View Related to Zone Detection Distances
Creating short fence or buried cable detection zones increases your ability to identify a threat by using your video surveillance system more effectively.
Plus, the DORI concept is particularly critical for protecting perimeters. Be sure to consider your viewing expectations in terms of Detection, Observation, Recognition, Identifiation (DORI). More details on DORI here.


Lightning and Surge Protection
There's understandable concern in the security industry when it comes to protecting equipment from lightning and other power surges. And putting cables along a metal fence around an entire perimeter just adds to the complexity level. In the video below, Tom Fontana and Tim Claus discuss the threat of power surge and how systems can be designed to minimize the risk.


Integration Options for Perimeter Detection
Common ways to integrate 3rd party systems like video management and access control with perimeter detection systems includes the use of contact closures and programming using a Software Development Kit (SDK) .


Fence Sensor Cable Repair
There can be significant risk involved when a fence intrusion detection system is compromised by a broken or damaged sensor cable. Joe Barnhart and Tim Claus walk us through a cable splice in this video.
Worth noting:
- It takes less than 15 minutes, minimal training, and only a couple common tools to repair damage to a copper-based fence intrusion detection sensor cable in most cases.


Stacked Microwave Detection Strategies
Using microwave detection to secure a perimeter is a strategy commonly used when a fence isn't an option or when multiple layers of security are required. Below, Tom Fontana and Tim Claus discuss the use of multiple microwave detection sensors and the technology involved that makes these strategies possible.
Helpful hints:
- The beam width and shape is fully dependent upon distance between the Tx and Rx devices and the flatness of the terrain between them.
- The goal is to achieve the highest possible alignment signal and use the lowest possible sensitivity setting. In most cases, customers will attain a basic alignment and then turn up sensitivity to compensate. This will cause poor performance and high NAR/FAR.
- Adjusting sensitivity is time consuming, plan for this during installation.


Armored Fence Sensor Cable Applications
To minimize the risk of suffering damage to a fence intrusion detection sensor cable, the use of armored cable is sometimes the best option. In this video, Tom Fontana and Tim Claus discuss the use of armored sensor cables and show us the difference.
In this video, we learn two primary applications for using armored cable:
- Rigid fence – armored sensor cable has an enhanced ability to mute high frequency vibrations on rigid fencing and nuisance alarm filtering in this application.
- High traffic areas – if the fence is next to a high traffic pedestrian area, then it may make sense to use armored cable. That way, if people are regularly handling or tampering with the cable, it doesn’t damage the actual sensor.


Site Survey
A site survey is necessary in order to properly evaluate the perimeter. Below is a link to Site Survey: Perimeter Detection to get you started down the path to an effective perimeter detection solution. The site survey will provide an opportunity for all stakeholders to set their expectations and will narrow down the best solution for the application.


Perimeter Detection Technologies
Various technologies can be used to detect organized motion, shock, vibration, and heat signature. These technologies include thermal imaging cameras, buried cable, fence mounted cable, infrared beam, stereo Doppler microwave, and radar in military or airport applications.


Thermal Imaging
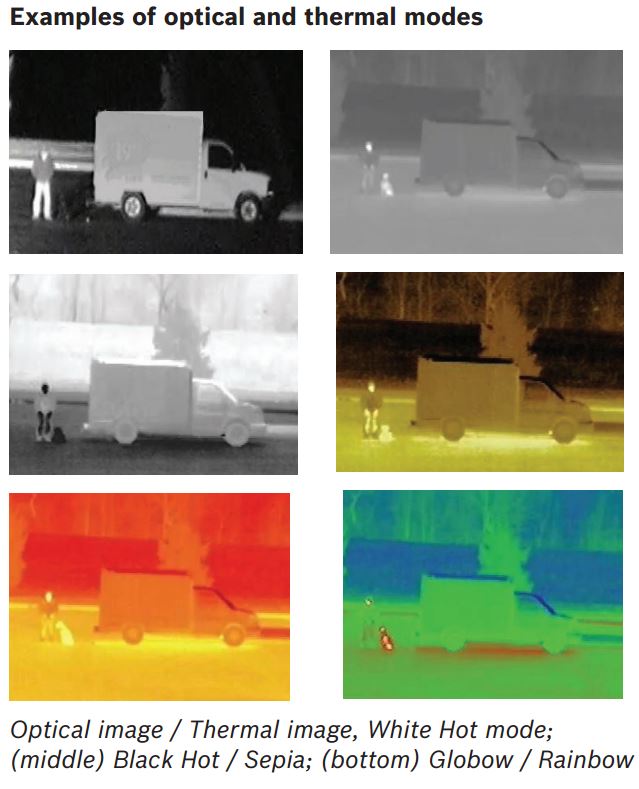 Thermal imaging cameras provide the opportunity to detect a human or other heat signature producing body at or before a perimeter. This technology allows monitoring stations to eliminate the possibility of cloaking by using shrubbery or camouflage clothing. Cameras that can see visible light are often used to verify a heat signature detected by a thermal camera since the resolution of a thermal imager is much lower than that of today’s high definition visible imagers. In many cases, lights will be turned on at the alarm site. Another option to provide light for the visible camera imager is to utilize infrared illumination which allows the camera to see a monochrome image of the scene with no visible light present.
Thermal imaging cameras provide the opportunity to detect a human or other heat signature producing body at or before a perimeter. This technology allows monitoring stations to eliminate the possibility of cloaking by using shrubbery or camouflage clothing. Cameras that can see visible light are often used to verify a heat signature detected by a thermal camera since the resolution of a thermal imager is much lower than that of today’s high definition visible imagers. In many cases, lights will be turned on at the alarm site. Another option to provide light for the visible camera imager is to utilize infrared illumination which allows the camera to see a monochrome image of the scene with no visible light present.
Thermal imaging cameras are available in many form factors. Most often a fixed camera is used, however, there are high end solutions which allow for pan tile zoom functionality. At the highest end of the camera capability range are thermal cameras with a second visible light sensor. This allows the operator to quickly switch between the thermal image and the visible image to quickly identify the potential threat.
Intelligent video analytics (IVA) are often deployed in conjunction with thermal camera sensors. The use of IVA allows for the facility owner to determine more specifically when a violation is occurring since the image from the sensor is not as detailed as that of a visible camera imager.
Fence Detection Systems

A fence detection system is used to detect cut or climb attempts by intruders attempting to gain site access. The detection cable, which is easily affixed to fence fabric or wire topper using cable ties, is connected to a processor module that analyzes vibration activity on the cable. A properly functioning fence detection system should alarm on intrusion attempts, but ignore environmental disturbances.
To ensure high probability of detection (Pd) and a low nuisance alarm rate (NAR), choose a fence detection system that may be calibrated in software on installation to account for variations in fence fabric or tension to ensure uniform detection sensitivity along the protected fence line. The system should also employ advanced digital signal processing capabilities that differentiate fence cut / climb attacks from harmless disturbances such as wind, rain or vehicle traffic, to successfully detect intrusions while preventing the nuisance alarms that plague other technologies. Insist on a system that precisely locates intrusion attempts to within 3m (10 ft) and that features software-controlled detection zone assignment (Free-Format Zoning™) to keep hardware costs low and maximize flexibility as needs change.
Unique Fence Sensor Applications
- Razor Wire - within the razor coil on top of a fence or wall
- Pipeline - applied to the outside of various types of pipelines to detect cutting, banging, and other disturbances
- Train Tracks - even if your facility perimeter fence is alongside a train track, you can still use a fence detection system when it's deployed properly
More about fence detection systems here
Buried Cable Detection Systems

A buried cable detection system provides volumetric (RF-based) detection of walking, running or crawling intruders. Designed for applications where covert protection is essential, cables are buried on the secure side of an existing physical barrier to prevent detection of animals or patrol officers, outside the barrier as an ‘early warning’ mechanism, or in place of a barrier if esthetics are of concern. RF energy couples between Tx and Rx cables to create an invisible RF-based detection field.
When evaluating buried technologies, select a system that requires minimal trenching for cable installation and no special ground preparation or graded cables that could result in increased cost or service time. Identify a system that may be calibrated in software on installation to properly address variations in ground composition or site conditions and achieve uniform detection along the protected area. Ensure that the system offers flexible, software-controlled detection zone assignment to cost-effectively address your site’s unique requirements, to successfully detect intrusions while preventing the nuisance alarms that plague other technologies. Most critically, look for advanced Digital Signal Processing capabilities that enable precise location of intruders to within 3m (10ft) but prevent harmless disturbances caused by small animals or environmental factors such as wind, rain or snow.
More about buried cable here
Microwave Sensors

Microwave sensors, also known as Radar, RF or Doppler sensors, detect walking, running or crawling human targets in an outdoor environment.
Microwave sensors generate an electromagnetic (RF) field between transmitter and receiver, creating an invisible volumetric detection zone. When an intruder enters the detection zone, changes to the field are registered and an alarm occurs.
Microwave sensors are often easy to install, provide high probability of detection, low nuisance alarms and resistance to rain, fog, wind, dust, falling snow and temperature extremes. Most operate at K-Band frequency, maximizing detection performance and minimizing interference from external radar sources.
More about microwave sensors here
Video Analytics
Camera systems can be deployed that use the information they "see" to alert authorities of very specific behavior violations such as line crossing in a specific direction as well as dozens of additional behaviors.
In the video below, we discuss the use video analytics and other systems to detect an intrusion into a secure area during a partner demonstration.
Active/Passive Infrared Sensors

Active infrared technology employs a two-column sensor for detection of intruders. The transmitter unit emits invisible active infrared beams. The receiver unit receives and analyses the beams and detects intruders passing between the two columns.
With passive infrared technology, intrusions are detected by sensing temperature (heat radiation) contrast between an intruder moving through the detection pattern and the background environment. Rugged construction, integrated heaters and self-adapting technology assure the reliable operation and constant detection capacity under changing environmental conditions or temperature extremes.
More on active infrared here
Dual Technology Motion Sensors

Dual technology motion sensors offer the unique combination of Doppler Microwave and passive infrared technology to provide volumetric protection for a variety of outdoor applications.
These sensors are configured for “And Gate” operation; both technology elements must activate simultaneously for the sensor to alarm. The microwave portion must detect motion of an intruder, while the passive infrared portion must detect infrared (heat) radiation emitted by an intruder.
Dual technology sensors feature a 15 m x 12 m (50 ft x 40 ft) detection pattern, and are specified for the protection of specific assets, strategic areas or as a gap-filler in conjunction with other detection systems such as fence or buried cable perimeter intrusion detection system, microwave links, or transceivers.
More about dual-technology motion detection here
Alarm Monitoring and Control Systems

Options include full color graphic map displays detailing precise alarm location and integrating data communications, event reporting and auxiliary security devices, to advanced security management tools incorporating live video and comprehensive assessment and reporting tools for centralized control of perimeter security operations across large or multiple sites.

Perimeter detection technology can significantly reduce nuisance alarms, however the need for alarm verification still exists. For this reason, most sites deploy force protection to an alarm site after verification of the alarm using a visible camera system. Most often this is accomplished using a pan tilt zoom camera system. PTZ cameras allow an operator to investigate a specific alarm zone along the perimeter without having to leave the command desk. By assessing the threat in advance, proper response can be deployed. The response may be a single guard or police officer who responds from a different site or from within the facility. These alarms may also be monitored by a 3rd party monitoring service located at a central monitoring station. The central monitoring station will then assess the alarm and activate an appropriate response.
In this video we see how a video management system can receive alarms from other systems, in this case a pull-station alarm, to cause an alert for an officer to react to instantly.
 Bosch VMS Information
Bosch VMS Information
 Genetec VMS Integration
Genetec VMS Integration
UNRIVALED PERFORMANCE, FLEXIBILITY AND LONG-TERM VALUE

Outdoor perimeter security is a facility’s first line of defense against attack, sabotage, property theft or harm to personnel, calling for great care in selecting an appropriate detection solution. A perimeter security system from Southwest Microwave ensures that your front line and critical inner perimeter elements are protected by proven, trusted technologies that deliver these industry-leading benefits:
- The highest detection performance and lowest nuisance alarm rates
- Industry-leading technical services and warranty coverage
- Approval by many of the world’s leading independent testing authorities
- The flexibility to evolve with your organization’s security needs
- Seamless connectivity - both between sensors and with your overall security program
- The product quality / resilience to operate reliably for years in harsh environmental conditions

Brochure (PDF)
WORLD-CLASS TECHNICAL SERVICES
Southwest Microwave’s pledge to provide world-class customer care is backed by extensive technical service capabilities. The system configuration and support experts in their Technical Services Group can handle your complete system needs – from design to implementation and beyond.
- SYSTEM PLANNING: Experienced project managers will assess your project and site parameters to customize a system that addresses budgetary and security goals. They can provide turnkey perimeter detection solutions or design a system to interface seamlessly with your existing security package.
- INSTALLATION AND COMMISSIONING SERVICES Their global network of factory-certified systems integrators can handle your complete installation requirements. Once installed, we offer factory commissioning of your detection system by highly qualified Southwest Microwave field service personnel to ensure peak performance.
- INDUSTRY-LEADING WARRANTY PROGRAM Southwest Microwave is serious about sensor performance. To reinforce the reliability of their systems and further broaden their value-to-investment ratio, Southwest Microwave offers five-year warranty protection on their complete range of perimeter security products.
- TRAINING AND SYSTEM SUPPORT Extensive product training backs every system Southwest Microwave delivers – ensuring that your equipment is installed and maintained according to factory specifications. Should you require post-sale technical support, their experienced service engineers are on call to assist you for the life of your system.
INTREPID™: Intelligent Sensors. Intelligent Choice.
Unique digital signal processing capabilities. Scalable networking and control options. User-friendly installation tools. Whether your goal is reliable intrusion detection, seamless integration or ease of deployment, INTREPID™ smart sensors offer best-in-class performance to handle the most challenging high-security applications in the harshest environmental conditions. INTREPID™ technologies are recognized to provide the highest probability of detection and lowest nuisance alarm rates, ensuring that your front line and critical inner perimeter elements are protected by proven, trusted technologies that evolve with your security needs.

INTREPID Brochure (PDF)
INTREPID™ Single-Platform Technologies: State-of-the-art detection capabilities. Seamless networking.
INTREPID™ Series II systems offer unique features and detection capabilities to reliably protect the highest security sites and perform in harsh climatic extremes. For unparalleled configuration and operating convenience, this advanced detection suite employs a common, open architecture communications protocol, universal set-up software, scalable system controllers and a broad input voltage range - reducing cost and complication traditionally associated with integrating multiple sensor technologies.
Finally, high-performance perimeter protection meets true systems convergence. With INTREPID’s single-platform sensor technologies, deploy any combination of fence, buried and digital microwave solutions on a unified network platform – to protect each portion of your perimeter with an optimal sensor for that location

INTREPID MicroPoint II Fence Detection (PDF)

INTREPID MicroTrack II Buried Cable (PDF)

INTREPID MicroWave 330 (PDF)
INTREPID™ High Security Standalone Sensors: Proven Perimeter Protection. Plug-and-Deploy Convenience
Southwest Microwave’s leading-edge standalone microwave and fence detection technologies offer unprecedented ease of set-up and deployment with user-friendly installation software, letting installers tailor a solution for the user’s individualized requirements in minutes.
These high-performance sensors incorporate advanced, proprietary digital signal processing (DSP) capabilities to optimize discrimination between intrusion attempts and environmental disturbances - mitigating risk of site compromise while effectively preventing nuisance alarms.


UniZone (PDF)


Model 336 (PDF)



 Thermal imaging cameras provide the opportunity to detect a human or other heat signature producing body at or before a perimeter. This technology allows monitoring stations to eliminate the possibility of cloaking by using shrubbery or camouflage clothing. Cameras that can see visible light are often used to verify a heat signature detected by a thermal camera since the resolution of a thermal imager is much lower than that of today’s high definition visible imagers. In many cases, lights will be turned on at the alarm site. Another option to provide light for the visible camera imager is to utilize infrared illumination which allows the camera to see a monochrome image of the scene with no visible light present.
Thermal imaging cameras provide the opportunity to detect a human or other heat signature producing body at or before a perimeter. This technology allows monitoring stations to eliminate the possibility of cloaking by using shrubbery or camouflage clothing. Cameras that can see visible light are often used to verify a heat signature detected by a thermal camera since the resolution of a thermal imager is much lower than that of today’s high definition visible imagers. In many cases, lights will be turned on at the alarm site. Another option to provide light for the visible camera imager is to utilize infrared illumination which allows the camera to see a monochrome image of the scene with no visible light present.






 Bosch VMS Information
Bosch VMS Information Genetec VMS Integration
Genetec VMS Integration 









